Hopefully by now you know, our business is cloud incident response. What if we told you, there are ways to prevent or limit the impact of an incident in the Micrsoft Azure cloud. Maybe you won’t even need us in the future. In this blog we’ll show you five low-cost and easy to implement measures with high-impact to prevent or limit the impact of an incident in Azure. In random order:
- Setup Azure Budget quotas and anomaly alerts
- Restrict app registration in Azure AD
- Prevent Subscriptions from entering or leaving your tenant
- Ingest Audit Logging for free
- Limit external collaboration
1. Azure Budget & Cost Anomaly
Everything you do in the cloud costs money. This also goes for attackers trying to do something in the cloud such as spinning up new resources or moving data out of your environment.
Azure Budgets enable you to establish spending thresholds and receive alerts when you’re nearing or surpassing those limits. This not only helps you stay in control of your finances but also ensures you’re aware of any unexpected usage spikes that could signal a potential incident.
The Azure Cost Analysis service is another method you can use to detect anomalous behaviour such as spikes in costs. You can set up an Anomaly alert to get notified for this type of activity. We will now show you how to setup both features.
Set Up an Azure Budget
- In the Azure Portal, navigate to “Cost Management and Billing”.
- Select Budgets and click on the “+ Add” button.
- Specify a budget amount and the desired timeframe for the budget.
- Define an alert threshold and configure alert recipients.
Now you’re not able to spend more than the threshold amount. You could even get warnings if a % of the amount was being used.

Configure a cost anomaly alert
- Go to Azure Cost Management
- Set the scope to the subscription you want to monitor (this only works on subscription level basis)
- Select “Cost Alerts” in the menu on the left
- Click on the “+ Add” button.
- Leave the default and specify email address where you want to be notified on and you’re ready to go.

2. Restrict app registration in Azure AD
Attacks leveraging Azure AD applications can be very difficult to spot especially if you’re using lots of applications in your environment. On top of that they’re often high impact as we’ve seen with recent incidents by a Chinese APT group and in the past with the SolarWinds incident.
By default everyone is allowed to register new applications, however you can and should limit the registration of new applications.
- Go to Azure Portal and select Azure Active Directory with an administrator account
- Go to “User Settings”
- Switch toggle to No for “Users can register applications” as shown in the screenshot below:

3. Prevent Subscriptions from entering or leaving your tenant
Subscription management is a crucial aspect of Azure governance. Preventing unauthorized subscriptions from entering your environment can prevent unanticipated surprises. Unauthorized subscriptions can lead to compliance issues, increased costs, and security vulnerabilities.
One attack scenario we have seen is Subscription transfers where an attacker transferred a subscription to a new tenant and took over effective control. The billing was still set to the billing account of our client, however they were locked out of the subscription and not able to remove the associated billing account, which resulted in serious damages.
To prevent subscriptions from entering/leaving your environment take the following steps:
- Go to Azure Portal and select Azure Active Directory with a Global Administrator
- Navigate to Subscriptions
- Select “Manage Policies” and switch toggle to “Permit no one” as shown in the below screenshot.

Use “Exempted Users” if you want to override this setting for specific users.
4. Ingest Audit Logging for free
Microsoft offers free audit logging for certain logs in Log Analytics or Sentinel. Allowing you to monitor activities across your environment. It’s strongly recommended configuring this in any environment, allowing you to detect and respond incidents faster. Microsoft does not charge for data in the following tables:
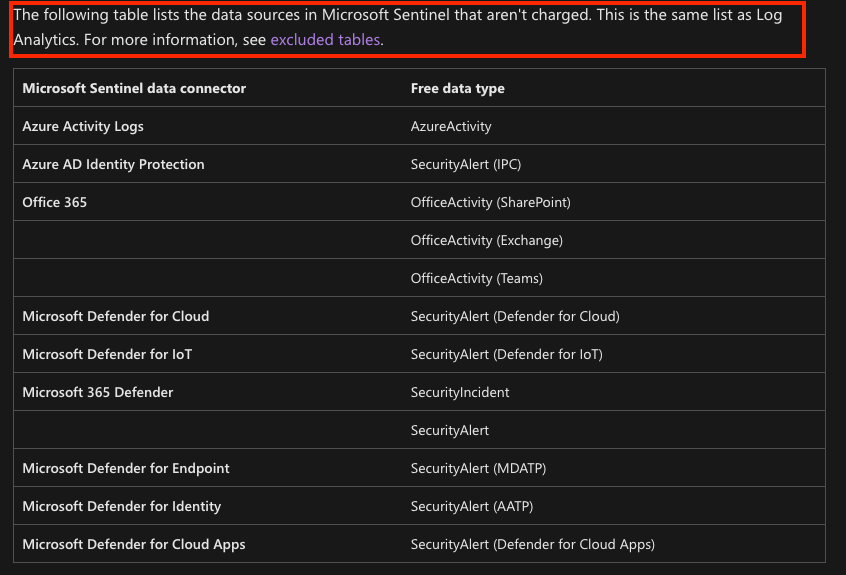
Especially the Azure Activity logs are useful, because they record activity inside a subscription such as executing RunCommands or creation of new resources.
5. Limit external collaboration
Lateral movement techniques have been a critical component of traditional compromises for years. With accelerated deployment of hybrid networks that combine on-premise and cloud infrastructure, attackers are looking for new tactics to achieve lateral movement in these new environments.
One way they do this is by misusing a feature called cross-tenant synchronization (CTS) in Azure Active Directory (AAD). This features lets organizations connect different parts of their network so people can use Microsoft and other apps from different parts of the network. This can be helpful for big companies that have different parts in different places, but still want to use the same apps.
Alternatively, attackers can use other tenants or guest accounts to allow for remote access in your environments. We suggest that if you don’t use any of this features to start disabling it.
External Collaboration settings
- Go to Azure Active Directory and select “User Settings”
- Select “Manage external collaboration settings”

- Modify Guest User access, the ability to send invites and self-service sign ups. Also limit Collaboration restrictions in order to prevent CTS from being used.
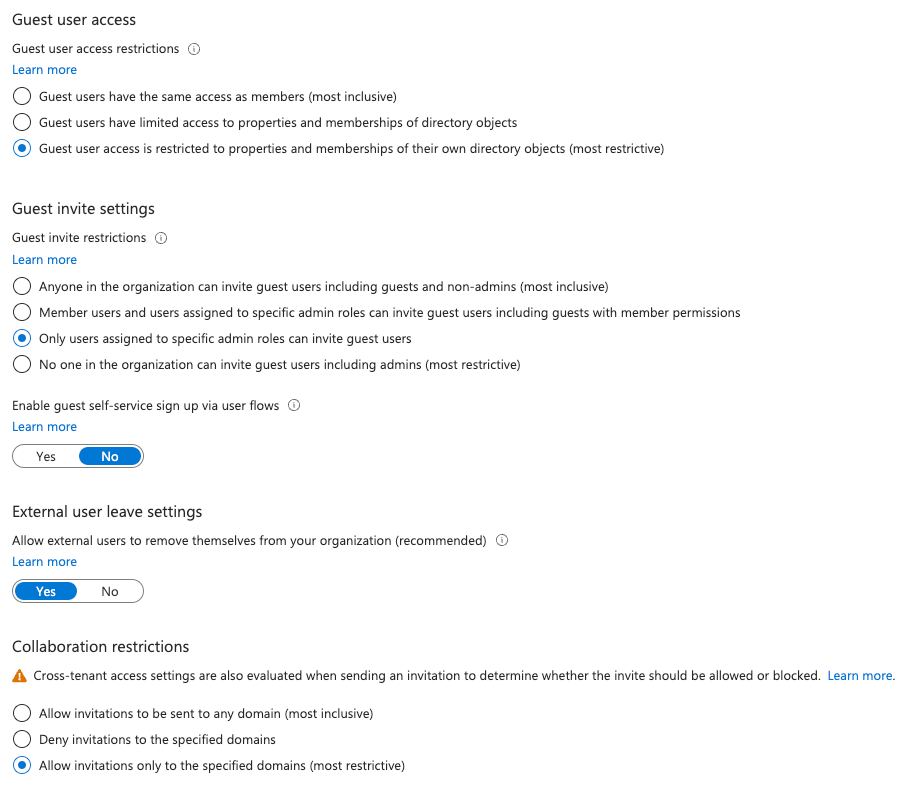
Important: If you need any of these settings to work you can override it on a per-user or use-case basis. In our opinion the defaults are far too permissive.
Conclusion
These five settings will prevent some incidents such as crypto-mining through budget quotas. Or app consent attacks by preventing users from accepting app registrations. Or they will limit the impact by providing means to investigate an attack through Log Analytics or Sentinel with the free logs. We hope you found the tips useful and feel free to share any additional ones you have.
Do you want us to review your Azure environment for signs of an active compromise or assess the forensic readiness of your cloud? Check out our pre-incident response services and contact us.
